Homepage » You are the firewall
How do I protect myself against Social Engineering & phishing?
Learn the tricks of criminal attackers to be armed against Social Engineering attacks and make your company more secure.
Nearly 9 out of 10 companies have been the victim of digital industrial espionage, sabotage, or data theft, resulting in damage of around 223 billion euros (source: bitkom). While in 2013 only 17% of all cyberattacks contained a Social Engineering component, today the vast majority of all attacks are already prepared through Social Engineering – the targeted manipulation of employees to gain access to sensitive information or to place malware on company computers.
This site offers you tools to arm yourself against social engineering attacks: What are the types of social engineering? What is the target of the attackers? How do they actually operate? How do I recognize a phishing e-mail? How do I recognize the target of a link? You will find answers to these questions here.
Have fun – and stay alert!

Content overview
Basic knowledge of Phishing & Social Engineering. Reading time: 12 minutes.
The term Social Engineering describes interpersonal techniques used to influence others in order to achieve a specific goal. When Social Engineering is combined with negative intentions, it can be used for malicious purposes. Social Engineering attacks use everyday social interactions (e.g., a phone call or email). The attacker tries to get the target person to follow certain prompts and thus gain access to information or company networks.
As protection by technical security systems becomes increasingly difficult to circumvent, Social Engineering is gaining in popularity: it is often technically impossible to detect such attacks. It is therefore essential that every employee pays attention to the topic of IT security and is aware of possible threats.
If Social Engineering attacks are successful, it is usually not due to deliberately malicious behavior on the part of employees. Attackers use various psychological tricks and social norms to create situations that are not perceived as dangerous at first. The following table lists various human behavior patterns and illustrates how they are exploited in Social Engineering attacks.
Behavior | Scenario | Possible Reaction | Possible Risk |
|---|---|---|---|
| Prejudice / Expectations | A technician requests access to the server room. | As a matter of course access is granted. | The technician’s clothing comes from a costume box, criminals can tap sensitive data undisturbed. |
| Deference to authority | The boss instructs an urgent payment to a new partner company from vacation. | The order is quickly complied with. | Criminals have exploited publicly available information to feign identity as realistically as possible (“boss scam”). |
| Curiosity | You find a USB stick in the parking lot and wonder who it belongs to? | The USB stick is connected to the computer to read it and identify the owner. | The USB stick contains malware that (unnoticed) infects the computer and the system. |
| Automatisms | Like every morning, you are about to answer your e-mails… | …and click on the link in a well-crafted phishing email. | The link redirects to a criminal fake website and automatically loads malware. |
| Fear | A notice from Amazon lands in your inbox: If you do not verify your account within a few days, a processing fee will be charged. | You verify your account – this happens unnoticed on a cloned login page. | Criminals have your login data and thus have access to your account. |
| Helpfulness | A supposed acquaintance of a colleague contacts you by e-mail about a problem and sends a file attachment. | The file is opened – perhaps you know some advice. | The file contains malware that (unnoticed) infects the computer and the system. |
In combination with time pressure and the demand for secrecy, criminals often achieve their goal quickly using these behavioral patterns.
The term phishing is based on the English word fishing and refers to a fraud attempt, usually carried out by e-mail. Figuratively speaking, it involves the fishing of passwords, whereby personal data is misused, or the owner of a bank account is to be harmed. Also, spy software, encryption Trojans or other files harmful to the computer system are often sent.
For example, you receive a genuine-looking email from a well-known company (Amazon, PayPal, Google, etc.), or even from their own colleague or boss. For targeted phishing attacks (spear phishing), perpetrators often collect useful information on social networks, job portals or the company website in advance to make the attack scenario as realistic as possible. Phishing emails often ask users to update login data, make important payments or enter credit card information. They also increasingly contain malicious files or lead to automatic malware downloads via attached links.
Falling for a phishing email can have far-reaching consequences. The following list gives some examples of how individuals and especially companies have been harmed by phishing.
Damage | Example |
|---|---|
Loss of login data | During the 2016 US election campaign, attackers gained access to the email account of Hillary Clinton’s campaign manager using a deceptively genuine account warning from Google. The information thus obtained caused massive damage to the presidential candidate. |
Transfers to unknown third parties | In 2016, the German automotive supplier Leoni AG was deceived by criminals with the so-called Boss Scam – and thus paid 40 million euros. |
IT system failure | Using encryption Trojans, entire companies or public institutions can be paralyzed for days and weeks. These are often ransomware (i.e., the encryption is linked to a ransom demand), such as Locky, WannaCry, or GoldenEye. In 2016, the IT of Lukaskrankenhaus in Neuss, Germany, was the victim of a ransomware attack. As a result, operations had to be postponed and emergencies rejected. |
Data loss | According to IBM Security, over 8 billion data records were captured in 2019 alone. |
Ransom demand | After encrypting the data on the computer and system, cybercriminals subsequently demand a ransom payment – if backups have not been made, the data will be lost and systems will be unusable. And also the import of backups costs time and money and demands valuable working time of colleagues. |
Industrial espionage | It is common and public knowledge that a large number of foreign states actively and constantly engage in economic espionage. They hire professional hacker groups that carry out targeted cyberattacks day after day. Attacks range from the placement of spy software, to the use of malware. |
Physical damage | Successful attacks can cause entire plants to fail. In 2014, for example, a blast furnace in Germany was severely damaged because malware that had been introduced prevented it from shutting down properly. |
Data privacy breaches | Major data breaches occur every day due to phishing attacks. Identity theft is just one example, along with the disclosure of sensitive company data, passwords or internal documents. |
In the following, we will show you various ways to protect yourself and your company from phishing and Social Engineering attacks.
The first rule here is to always be skeptical and vigilant. If a message looks suspicious, the sender should be contacted directly about the email via a known channel. In most cases, a short phone call or an inquiry in the internal short message service is sufficient for this. There’s no silly question here: if ten false positives help prevent an attack, it saves the IT department a lot of time and hassle.
Sometimes phishing e-mails are already noticed as fake by their sender address: Attackers use sender addresses such as. @amazon-shipping.com instead of @amazon.com or @it-seal.de-index.de instead of @it-seal.de to feign legitimacy. However, in most cases, the sender address of an e-mail is as easy to forge as that of a letter – so even a supposedly legitimate sender offers no security!
The following points often indicate that the message is fraudulent:
Anomalies | Explanation |
|---|---|
Unusual writing style, deceptive subject, grammatical and spelling errors | Doesn’t the colleague usually write more openly and casually? Be skeptical! To some extent, fake emails stand out due to grammatical errors or nonsensical words, as the messages are often translated using an online translation service. |
Missing name / unusual form of address | A bank or a partner company would never address you as “Dear Mr. Customer”, since the bank or the partner is likely to know your name. |
Urgent need for action is generated | You are asked to act quickly – sometimes this is even combined with a threat. You should also be suspicious here. Get a second opinion from a colleague or call the sender directly and ask. |
Request to enter data | Passwords, PINs and TANs are never requested over the phone from colleagues, your favorite online mail order company or a bank; this is among the most important security rules. |
Request to open a file / activate edit mode | In unexpected emails, you should never download or open files, because they may contain malware and infect your computer. |
Inserted HTML links or forms | Hyperlinks should always be checked before clicking on them. Pay close attention to where the link leads to. A detailed explanation of how to check the destination of a link can be found in the next section. |
Hyperlinks are pieces of text that, when clicked, call up the associated target. This is usually a web page. While in some phishing emails parts of the text are linked and underlined (e.g. “…you can find here.”), others may show the whole link. However, both elements may hide a different link target. To recognize this, move the mouse over the link without clicking. Now, in the window of the program in question (e.g. your email client), the real target is displayed at the bottom left corner or below the mouse. On mobile devices, the real target becomes visible when the link is touched and held for two seconds.
Examine the link target closely: the relevant part of a link can be found in the so-called “who section”. If you read from http(s):// to the next “/”, it is around the last dot before the “/”. The rest of the link is completely negligible. In the following examples, the “who area” is marked in bold.
Safe example: https://www.google.com/services leads to google.com.
Phishing example: https://www.google.com.myaccounts.biz/services leads to myaccounts.biz.
If you are ever unsure about the destination of a link, you can have it checked at www.virustotal.com.
Phishing attacks work particularly well when they are designed to be as realistic as possible. To do this, the attacker needs information about his target person. With so-called spear phishing, criminals use publicly available information on social media such as Facebook or Instagram, on professional social media networks such as Xing or LinkedIn, on news sites or on the company website. Therefore, the first and most important recommendation is: data thrift. Check what information you disclose and to whom. Contacts, position in the company or interests are of particular interest. For example, check your privacy settings on LinkedIn wisely so that your contacts are not publicly viewable.
Furthermore, regular updates are essential, e.g., to prevent attacks via browser or plugin vulnerabilities. Outdated versions may contain security vulnerabilities that make it very easy for attackers to infect your computer. With many operating systems, updates are only installed when you reboot. Therefore, do not just switch your computer to stand-by, but turn it off completely on a regular basis.
In the past, the Adobe Flash Player browser extension in particular has repeatedly attracted attention due to security vulnerabilities. It is required to display certain content on websites. In various attacks, computers were infected unnoticed just by visiting a website. Therefore, select the settings so that Flash Player is disabled by default and only runs after your consent.
Listen to your gut feeling! There are often small inconsistencies in a phishing e-mail that are often overlooked in the stress of everyday life or due to automatic mechanisms. As soon as even a small question mark appears, check the email more closely. You have learned to recognize fake links. You can have your virus scanner check file attachments before opening them. To do this, download the file and select the appropriate option after right-clicking. Special care should be taken with MS Office documents containing macros (e.g. .docm): these can load malicious code when the macros are activated and are not usually detected by virus scanners. Therefore, only activate macros if the origin of the document is absolutely trustworthy. Currently .zip files are also frequently used by criminals. Even opening them can result in the execution of malware. If you are not sure: Ask. Ask the sender, your IT department or your colleagues.
If you feel that you have fallen for a phishing attack, you should react quickly. The longer you wait, the greater the potential damage might be. The right response depends on the nature of the mistake.
If you have shared your password by entering it on a fake login page, you should change this password immediately or have the account suspended.
If you may have downloaded malware, you should immediately unplug the network cable and disconnect the computer from the Wi-Fi.
In any case, you should immediately inform the IT department about the incident.
Many phishing e-mails are difficult for virus scanners and firewalls to recognize as such, because they often do not contain malware as a file attachment, but rather load it afterwards. This is done via an inserted link that, when clicked on, initiates the download of a file by means of a so-called “drive-by download” without any further intervention. Attacks such as the “boss scam” even manage without any malware at all: The payment instruction allegedly requested by a member of management consists of pure text, and is therefore impossible to detect technically.
Therefore people are increasingly the focus of attack among cyber criminals, as they can represent an organization’s greatest security vulnerability. However, if he is armed, he simultaneously offers great potential to achieve a high level of security. That is why it is so important that every employee is sensitized to the topic of phishing, recognizes attacks of this type with certainty and knows how to behave professionally.
For this purpose, IT-Seal GmbH offers with the Security Awareness Training the possibility to conduct a Phishing Awareness Training in the company. On the one hand, this measures the security standard against social engineering attacks in the company, and on the other hand, it makes it possible to bring the knowledge and security awareness of the employees up to date. Every time a “wrong” click is made on our phishing e-mails, all participants are shown immediately and with little effort how to recognize phishing attacks and how to handle them professionally by means of a so-called teachable moment.
We recommend the following tools to both private users and companies alike:
- With the free learning concept NoPhish, the basic rules of phishing detection can be learned in a playful way. It is available both as an online platform and as an iOS and Android app. NoPhish was developed by SECUSO, a research group at KIT.
- If you use Thunderbird as your email client, you can download the Torpedo add-on. This tool helps you to detect malicious links. Torpedo was developed by SECUSO, a research group at KIT.
- PassSec+ for Mozilla Firefox detects unencrypted websites and warns you when you enter login data. This way you are protected against many attacks that try to steal login data. PassSec+ was developed by SECUSO, a research group of KIT.
- If your gut feeling warns you: At www.virustotal.com you can have links checked if you are not sure about the real target of the link. Files can also be checked here – but be careful
Use different passwords for different accounts and change them regularly – otherwise, in the worst case, potential attackers will have access everywhere. A password manager (e.g. KeePass oder KeePassXC) can help to keep track: With it, you only need to remember one master password.

Behind IT-Seal (Social Engineering Analysis Labs) are IT security experts for building a sustainable security culture. We help companies and their employees to reduce the dangers and damages caused by social engineering attacks to a minimum. For this purpose, respectful but effective and authentic attack simulations are carried out. On the one hand, this makes the company’s security standard measurable, and on the other hand, all participants learn how to deal with cyber attacks in a safe environment. The simulation of attacks is usually carried out by e-mail and involves different levels of difficulty. The work and data protection of the participating employees is always our top priority. In our phishing evaluations, we only report on group-related behavior – individual behavior is not communicated at any time.
We pursue a full-service concept and offer needs-based training with our innovative Awareness Engine: participants who are already confident in recognizing phishing attacks are not disturbed in their daily work. However, if an employee clicks on one of our phishing e-mails, they will be shown directly on the example of this e-mail how they could have unmasked it as such. Thus, each participant receives as much training as necessary, but as little as possible.
The goal is to support companies in establishing an actively practiced security culture based on sustainably sensitized employees who know and accept their responsibility for the company. Everyone pulls together to increase the safety of their company.
Does this sound interesting? Try our free phishing simulation: As a participant in our demo, you will receive four phishing emails within two business days. If you click (by mistake or out of curiosity) on a link included, you will land on our explanation page.
Security awareness made measurable with our ESI®: The Employee Security Index is a scientific benchmark for measuring IT security awareness in organizations. It also enables comparability. How does my participant groups compare against each other or against other companies in my industry? Where are measures still needed? The ESI®, a key performance indicator for information security, makes this visible.
Guarding against spear phishing by criminals: To make employees as aware as possible of attacks by cyber criminals, we have developed a patented spear phishing engine. This collects publicly available information from professional networks (Open Source Intelligence, OSINT for short) and, based on this, creates realistic spear phishing simulations with personalized addressing and authentic content. We want employees to be able to train for the real thing with realistic and confidence-inspiring messages. We don’t do generic “mass phishing.”
Our co-founder and CEO David Kelm is an accomplished Social Engineering expert: David Kelm has been studying Social Engineering (employee manipulation by criminals) since 2012. Kelm won the “Best Student Award” from the German Federal Office for Information Security (BSI) for his scientific findings on the “human factor” in IT security. He is convinced that with the right learning approach, employees can become the “human firewall” of their company – instead of compromising its security.
Our work is based on scientific findings: Our employee awareness measures against spear phishing, as well as how they measure success, are based on successful research. With David Kelm, our start-up, which is a spin-off of the Technical University of Darmstadt, also has an accomplished expert in Social Engineering, especially spear phishing, at its helm.
Data privacy and employee friendliness go hand in hand: Since we want to sensitize employees but not blacken their names, we make sure that they always remain anonymous during the evaluation. We only evaluate the success of our measures on a group basis, and our data processing is of course GDPR-compliant.
Made in Germany: IT-Seal GmbH is a German company that specializes mainly in the German market. Business customers based here therefore receive GDPR-compliant services from us, which also comply with the legal provisions applicable here in other respects. Already during the development of our solutions, employee and data protection are in the foreground for us (“security & privacy by design”).
Germany’s first local cyber security campaign: With “Bleib wachsam, Darmstadt!” (Stay alert, Darmstadt!), we have launched an unprecedented initiative with Darmstadt, the city of science, and Darmstadt, the digital city, to offer citizens free IT security training and raise their awareness of phishing.
Multiple awards: We won the following awards for our measures around employee sensitization and our ideas for measuring and comparing them:
– 1st place as “Best Cybersecurity Startup in Germany” at it-sa.
– 1st place at the Europe-wide Social Engineering competition of the TREsPASS_Project
– “Top 10 Best Cyber Security Startups in Europe” at the SBA Research Competition
– “Best Student Award” of the German Federal Office for Information Security (winner: our co-founder and idea provider David Kelm)
You can find more about us on “Why IT-Seal?” Do you have any questions? We look forward to hearing from you!
Homepage » You are the firewall
WIE SCHÜTZE ICH MICH GEGEN SOCIAL ENGINEERING & PHISHING?
Lernen Sie die Tricks der kriminellen Angreifer kennen, um gegen Social Engineering-Angriffe gewappnet zu sein und Ihr Unternehmen sicherer zu machen.
Allein in Deutschland wurde jedes zweite Unternehmen bereits Opfer von digitaler Wirtschaftsspionage, Sabotage oder Datendiebstahl, dabei entstand ein Schaden von rund 43 Mrd. Euro (Quelle: bitkom). 19% der Angriffe fielen in den Bereich “Social Engineering” – die gezielte Manipulation von Mitarbeitern, um Zugang zu sensiblen Informationen zu erhalten oder Schadsoftware auf Firmenrechnern zu platzieren.
Die Bleib Wachsam-Kampagne von IT-Seal bietet Ihnen ein Werkzeug, sich gegen Social Engineering-Angriffe zu wappnen: Welche Arten von Social Engineering gibt es? Was ist das Ziel der Angreifer? Wie wird konkret vorgegangen? Wie erkenne ich eine Phishing-E-Mail? Wie erkenne ich das Ziel eines Links? Auf diese Fragen finden Sie hier eine Antwort.
Viel Spaß – und bleiben Sie wachsam!

INHALTSÜBERSICHT
Basiswissen Phishing & Social Engineering. Lesezeit: 12 Minuten.
Der Begriff Social Engineering beschreibt zwischenmenschliche Techniken zur Beeinflussung anderer, mit deren Hilfe ein bestimmtes Ziel erreicht werden soll. Wird Social Engineering mit negativen Absichten vereint, kann es für schadhafte Zwecke eingesetzt werden. Bei Social Engineering-Angriffen werden alltägliche soziale Interaktionen (z.B. ein Telefongespräch oder eine E-Mail) genutzt. Der Angreifer versucht, die Zielperson dazu zu bringen, bestimmten Aufforderungen zu folgen und so Zugang zu Informationen oder Firmennetzwerken zu erlangen.
Da der Schutz durch technische Sicherheitssysteme immer schwieriger zu umgehen ist, gewinnt Social Engineering an Beliebtheit: Oft ist es technisch unmöglich, solche Angriffe zu erkennen. Daher ist es unabdingbar, dass jeder Mitarbeiter dem Thema IT-Security Aufmerksamkeit schenkt und sich möglicher Bedrohungen bewusst ist.
Sind Social Engineering-Angriffe erfolgreich, dann liegt das meist nicht an absichtlich böswilligem Verhalten der Mitarbeiter. Angreifer nutzen verschiedene psychologische Tricks und soziale Normen, um Situationen zu schaffen, die im ersten Moment als nicht gefährlich wahrgenommen werden. Die folgende Tabelle listet verschiedene menschliche Verhaltensmuster auf und verdeutlicht, wie diese bei Social Engineering-Angriffen ausgenutzt werden.
Verhalten | Szenario | mögliche Reaktion | mögliches Risiko |
|---|---|---|---|
Vorurteile / Erwartungen | Ein Techniker verlangt Zutritt zum Serverraum. | Der Zutritt wird selbstverständlich gewährt. | Die Technikerkleidung stammt aus der Kostümkiste, Kriminelle können ungestört sensible Daten abgreifen. |
| Autoritätshörigkeit | Der Chef weist aus dem Urlaub eine dringende Zahlung an ein neues Partnerunternehmen an. | Der Anweisung wird schnell Folge geleistet. | Kriminelle haben öffentlich zugängliche Informationen ausgenutzt, um die Identität möglichst realistisch vorzutäuschen (“Chef-Masche”). |
| Neugierde | Sie finden einen USB-Stick auf dem Parkplatz. Wem er wohl gehört? | Der USB-Stick wird ausgelesen, um den Besitzer zu identifizieren. | Der USB-Stick beinhaltet Schadsoftware, die (unbemerkt) den Rechner und das System infiziert. |
| Automatismen | Wie jeden Morgen sind Sie dabei, Ihre E-Mails zu beantworten… | …und klicken auf den Link in einer gut gemachten Phishing-E-Mail. | Der Link leitet auf eine kriminelle Fake-Website und lädt automatisch Schadsoftware nach. |
| Angst | Ein Hinweis von Amazon landet in Ihrem Postfach: Sollten Sie Ihr Konto nicht innerhalb von wenigen Tagen verifizieren, wird eine Bearbeitungsgebühr fällig. | Das Konto wird verifiziert – dies geschieht unbemerkt auf einer geklonten Login-Seite. | Kriminelle verfügen über Ihre Zugangsdaten und haben so Zugriff auf Ihr Konto. |
| Hilfsbereitschaft | Ein angeblicher Bekannter einer Kollegin wendet sich per E-Mail wegen eines Problems an Sie und sendet einen Dateianhang. | Die Datei wird geöffnet – vielleicht weiß man Rat. | Die Datei beinhaltet Schadsoftware, die (unbemerkt) den Rechner und das System infiziert. |
In Kombination mit Zeitdruck und der Aufforderung zu Verschwiegenheit kommen Kriminelle unter Nutzung dieser Verhaltensmuster oft schnell an ihr Ziel.
Der Begriff Phishing ist an das englische Wort fishing (engl. für Angeln, Fischen) angelehnt und bezeichnet einen meist per E-Mail durchgeführten Betrugsversuch. Bildlich gesprochen geht es um das Angeln von Passwörtern, wodurch persönliche Daten missbraucht oder der Inhaber eines Bankkontos geschädigt werden sollen. Außerdem werden häufig Spionagesoftware, Verschlüsselungstrojaner oder andere für das Computersystem schädliche Dateien versendet.
Sie erhalten beispielsweise eine echt wirkende E-Mail von einem bekannten Unternehmen (Amazon, PayPal, Google, etc.), oder sogar von ihrem eigenen Kollegen oder Chef. Für gezielte Phishing-Angriffe (Spear Phishing) sammeln Täter oftmals im Vorfeld nützliche Informationen auf sozialen Netzwerken, Jobportalen oder der Unternehmenswebsite, um das Angriffsszenario möglichst realistisch zu gestalten. Phishing-E-Mails fordern oft dazu auf, Login-Daten zu aktualisieren, wichtige Zahlungen auszuführen oder Kreditkarteninformationen einzugeben. Außerdem enthalten sie immer öfter auch schädliche Dateien oder führen über beigefügte Links zu automatischen Downloads von Schadsoftware.
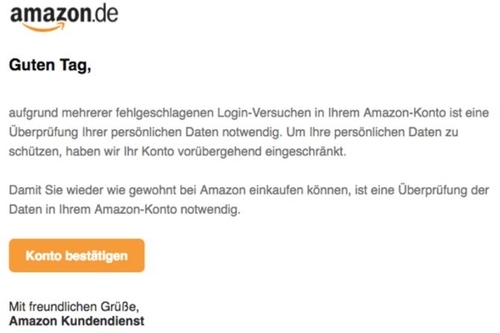

Fällt man auf eine Phishing-E-Mail herein, kann das weitreichende Folgen mit sich bringen. Die folgende Liste nennt einige Beispiele, wie Privatpersonen und insbesondere Unternehmen von Phishing geschädigt wurden.
Schaden | Beispiel |
|---|---|
Verlust von Login-Daten | Während des US-Wahlkampfs 2016 erlangten Angreifer mit einer täuschend echten Accountwarnung von Google Zugang zum E-Mail-Account des Wahlkampfmanagers von Hillary Clinton. Die so erhaltenen Informationen schädigten die Präsidentschaftskandidatin massiv. |
Überweisungen an unbekannten Dritten | Der deutsche Automobilzulieferer Leoni AG wurde 2016 mit der sogenannten Chef-Masche von Kriminellen in mehreren Runden um 40 Millionen Euro erleichtert. |
Ausfall von IT-Systemen | Mittels Verschlüsselungstrojanern können ganze Unternehmen oder öffentliche Einrichtungen über Tage und Wochen hinweg lahm gelegt werden. Oft handelt es sich um Ransomware (d.h. die Verschlüsselung ist mit einer Lösegeldforderung verbunden), wie z.B. Locky, WannaCry oder GoldenEye. 2016 wurde die IT des Lukaskrankenhaus in Neuss Opfer eines Ransomware-Angriffs. Dies hatte zur Folge, dass Operationen verschoben und Notfälle abgelehnt werden mussten. |
Verlust von Daten | Allein im Jahr 2016 Jahr wurden IBM Security zufolge über vier Milliarden Datensätze erbeutet. |
Forderung von Lösegeldzahlungen | Nach Verschlüsselung der Daten auf dem Rechner und dem System verlangen Cyberkriminelle anschließend eine Lösegeldforderung – falls keine Backups durchgeführt wurden, sind sonst die Daten verloren und Systeme nicht benutzbar. Und auch die Einspielung von Backups kostet Zeit und Geld und fordern wertvolle Arbeitszeit der Kollegen. |
Wirtschaftsspionage | Es ist allgemein und öffentlich bekannt, dass eine Vielzahl ausländischer Staaten aktiv und ständig Wirtschaftsspionage betreibt. Sie beauftragen professionelle Hackergruppen, die Tag für Tag gezielte Cyberattacken ausführen. Angriffe reichen von der Platzierung von Spionagesoftware, bis hin zum Einsatz Schadsoftware. |
Physikalische Schäden | Erfolgreiche Angriffe können zu Ausfällen ganzer Anlagen führen. 2014 wurde in Deutschland beispielsweise ein Hochofen stark beschädigt, da eine eingeschleuste Schadsoftware verhinderte, dass er ordnungsgemäß heruntergefahren werden konnte. |
Verletzungen des Datenschutzes | Täglich kommt es durch Phishing-Attacken zu großen Datenschutzverstößen. Identitätsdiebstahl ist nur ein Beispiel, neben der Weitergabe von sensiblen Unternehmensdaten, Passwörtern oder interner Dokumente. |
Im Folgenden zeigen wir Ihnen verschiedene Möglichkeiten auf, wie Sie sich und Ihr Unternehmen vor Phishing- und Social Engineering-Angriffen schützen können.
Die oberste Regel ist hierbei, stets skeptisch und wachsam zu sein. Wirkt eine Nachricht verdächtig, sollte der Absender über einen bekannten Weg direkt auf die E-Mail angesprochen werden. Meistens genügt dafür schon ein kurzer Anruf oder eine Anfrage im internen Kurznachrichtendienst. Es gibt dabei keine dumme Frage: Wenn zehn Fehlalarme helfen, einen Angriff zu verhindern, spart das der IT-Abteilung viel Zeit und Ärger.
Manchmal fallen Phishing-E-Mails schon durch ihren Absender als gefälscht auf: Angreifer nutzen Absenderadressen wie z.B. @amazon-versand.de statt @amazon.de oder @it-seal.de-index.de statt @it-seal.de, um Legitimität vorzutäuschen. Jedoch ist in den meisten Fällen die Absenderadresse einer E-Mail so einfach zu fälschen wie die eines Briefs – auch ein vermeintlich legitimer Absender bietet demnach keine Sicherheit!
Folgende Punkte lassen oft erkennen, dass es sich um eine betrügerische Nachricht handelt:
Auffälligkeiten | Erklärung |
|---|---|
Ungewöhnlicher Schreibstil, trügerischer Betreff, Grammatik- und Orthografiefehler | Schreibt der Kollege nicht eigentlich offener und lockerer? Seien Sie skeptisch! Zum Teil fallen gefälschte E-Mails durch Grammatikfehler oder unsinnige Wörter auf, da die Nachrichten häufig mit einem Online-Übersetzungsdienst übersetzt werden. |
Fehlender Name / ungewöhnliche Ansprache | Eine Bank oder ein Partnerunternehmen würde Sie niemals mit “Sehr geehrter Herr Kunde” ansprechen. |
Dringender Handlungsbedarf wird erzeugt | Sie werden aufgefordert, schnell zu handeln – manchmal ist dies sogar mit einer Drohung verbunden. Hier sollten Sie ebenfalls stutzig werden. Holen Sie sich eine zweite Meinung von einem Kollegen oder rufen Sie direkt beim Absender an und fragen Sie nach. |
Aufforderung zur Eingabe von Daten | Passwörter, PIN und TANs werden niemals telefonisch von Kollegen, von Ihrem Lieblings-Online-Versandhaus oder einer Bank abgefragt; dies zählt zu den wichtigsten Sicherheitsregeln. |
Aufforderung zur Öffnung einer Datei / Aktivierung des Bearbeitungsmodus | In unerwarteten E-Mails sollten Sie keinesfalls Dateien herunterladen oder öffnen, denn diese können Schadsoftware enthalten und Ihren Computer infizieren. |
Eingefügte HTML Links oder Formulare | Hyperlinks sollten immer überprüft werden, bevor sie angeklickt werden. Hierbei ist genau darauf zu achten, wohin der Link führt. Eine ausführliche Erklärung, wie Sie das Ziel eines Links überprüfen, finden Sie im nächsten Abschnitt. |
Hyperlinks sind Textteile, die beim Anklicken das damit verknüpfte Ziel aufrufen. Dabei handelt es sich meistens um eine Webseite. Während in manchen Phishing-E-Mails Teile des Texts verlinkt sind (z.B. “…finden Sie hier.”), ist oft auch ein ganzer Link dargestellt. Hinter beiden Elementen kann sich jedoch ein anderes Link-Ziel verbergen. Um dieses zu erkennen, bewegen Sie die Maus über den Link, ohne zu klicken. Nun wird im Fenster des betreffenden Programms unten links oder unter der Maus das echte Ziel angezeigt. Auf Mobilgeräten wird das echte Ziel sichtbar, wenn der Link für zwei Sekunden berührt gehalten wird.
Untersuchen Sie das Link-Ziel genau: Den relevanten Teil eines Links findet man im sogenannten “Wer-Bereich”. Liest man vom http(s):// zum nächsten “/”, befindet er sich um den letzten Punkt herum vor dem “/”. Der Rest des Links ist vollständig vernachlässigbar. In den folgenden Beispielen ist der Wer-Bereich fett markiert.
Sicheres Beispiel: https://www.google.de/services führt auf google.de.
Phishing-Beispiel: https://www.google.de.myaccounts.biz/services führt auf myaccounts.biz.
Schauen Sie sich die folgenden Links an und achten Sie auf den Wer-Bereich: Welche Links sind echt, und welche gefälscht?
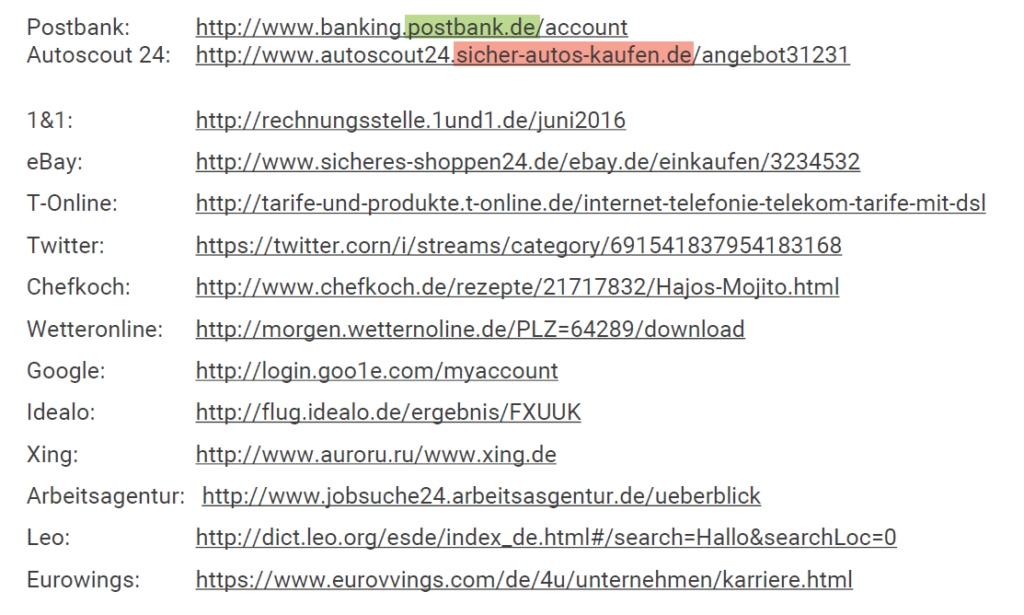
Hier kommen Sie zur Auflösung – aber prüfen Sie den Link, bevor Sie klicken!
Falls Sie sich unsicher sind, was das Ziel eines Links angeht, können Sie diesen auf www.virustotal.com prüfen lassen.
Falls Sie sich unsicher sind, was das Ziel eines Links angeht, können Sie diesen auf www.virustotal.com prüfen lassen.
Phishing-Angriffe funktionieren besonders dann gut, wenn sie möglichst realistisch gestaltet sind. Dazu benötigt der Angreifer Informationen über seine Zielperson. Beim sogenannten Spear Phishing nutzen Kriminelle öffentlich einsehbare Daten auf sozialen Medien wie Facebook oder Instagram, auf Jobportalen wie Xing oder Linkedin, auf Nachrichtenseiten oder auf der Unternehmenswebsite. Daher lautet die erste und wichtigste Empfehlung: Datensparsamkeit. Überprüfen Sie, welche Informationen Sie wem preisgeben. Besonders interessant sind dabei Kontakte, die Position im Unternehmen oder Interessen. Wählen Sie z.B. Ihre Datenschutzeinstellungen auf Xing so, dass Ihre Kontakte nicht öffentlich einsehbar sind.
Des Weiteren sind regelmäßige Updates unumgänglich, um z.B. Angriffen über Browser- oder Plugin-Schwachsstellen vorzubeugen. In veralteten Versionen können Sicherheitslücken bestehen, die es für Angreifer sehr einfach machen, Ihren Rechner zu infizieren. Bei vielen Betriebssystemen werden Updates erst beim Neustart installiert. Schalten Sie Ihren Rechner daher nicht nur auf Stand-By, sondern schalten Sie ihn regelmäßig ganz aus.
In der Vergangenheit ist vor allem das Browser-Plugin Adobe Flash Player wiederholt durch Sicherheitslücken aufgefallen. Es wird zum Anzeigen bestimmter Inhalte auf Webseiten benötigt. Bei verschiedenen Angriffen wurden Rechner allein durch den Besuch einer Webseite unbemerkt infiziert. Wählen Sie die Einstellungen daher so, dass der Flash Player standardmäßig deaktiviert ist und nur nach Ihrer Zustimmung ausgeführt wird.
Hören Sie auf Ihr Bauchgefühl! In einer Phishing-E-Mail gibt es oft kleine Unstimmigkeiten, die im Alltagsstress oder aufgrund von Automatismen häufig übersehen werden. Sobald auch nur ein kleines Fragezeichen aufkommt, überprüfen Sie die E-Mail genauer. Sie haben gelernt, gefälschte Links zu erkennen. Dateianhängen können Sie vor dem Öffnen von Ihrem Virenscanner prüfen lassen. Laden Sie dazu die Datei herunter und wählen Sie nach einem Rechtsklick die entsprechende Option aus. Besondere Vorsicht ist bei MS Office-Dokumenten mit Makros geboten (z.B. .docm): Diese können beim Aktivieren der Makros Schadcode nachladen und werden üblicherweise nicht von Virenscannern erkannt. Aktivieren Sie Makros daher nur, wenn der Ursprung des Dokuments absolut vertrauenswürdig ist. Auch .zip-Dateien werden von Kriminellen aktuell häufig verwendet. Hier kann schon das Öffnen die Ausführung von Schadsoftware zur Folge haben.Wenn Sie sich nicht sicher sind: Fragen Sie nach. Beim Absender, bei der IT-Abteilung oder bei Kollegen.
Wir empfehlen das fünfminütige Aufklärvideo “Online-Betrug – Gefahren erkennen und abwehren“.
Lizenz: CC BY-SA 4.0: https://creativecommons.org/licenses/by-sa/4.0
Ein Film von: Design & Animation MotionEnsemble, Idee / Konzept: Prof. Dr. Melanie Volkamer (secuso.org) & Alexander Lehmann (alexanderlehmann.net), Stimme Florian Maerlender (www.maerlender.eu)
https://www.youtube.com/watch?v=XeslAkZIuwY
Falls Sie das Gefühl haben, auf einen Phishing-Angriff hereingefallen zu sein, sollten Sie schnell reagieren. Umso länger Sie warten, desto größer ist unter Umständen der potentielle Schaden. Die richtige Reaktion hängt von der Art des Fehler ab.
Wenn Sie Ihr Passwort durch Eingabe auf einer gefälschten Login-Seite weitergegeben haben, sollten Sie dieses Passwort sofort ändern oder das Konto sperren lassen.
Wenn Sie möglicherweise Schadsoftware heruntergeladen haben, sollten Sie sofort das Netzwerkkabel herausziehen und die Verbindung des Rechners vom W-LAN trennen.
In jedem Fall sollten Sie unverzüglich die IT-Abteilung über den Vorfall informieren.
Viele Phishing-E-Mails sind für Virenscanner und Firewalls nur schwer als solche zu erkennen, da sie häufig keine Schadsoftware als Dateianhang enthalten, sondern diese erst nachladen. Dies geschieht über einen eingefügten Link, der beim Anklicken durch einen sogenannten “Drive-by-Download” ohne weiteres Zutun das Herunterladen einer Datei initiiert. Angriffe wie die Chef-Masche kommen sogar ganz ohne Schadsoftware aus: Die angeblich von einem Mitglied des Managements geforderte Zahlungsanweisung besteht aus reinem Text, und ist daher unmöglich technisch zu erkennen.
Deshalb steht der Mensch als Schwachstelle bei Cyber-Kriminellen immer öfter im Fokus des Angriffs, denn er kann die größte Sicherheitslücke einer Organisation darstellen. Ist er jedoch gewappnet, bietet er gleichzeitig ein großes Potential, um ein hohes Sicherheitsniveau zu erreichen. Daher ist es so wichtig, dass jeder Mitarbeiter für das Thema Phishing sensibilisiert wird, Angriffe dieser Art sicher erkennt und weiß, wie man sich professionell verhält.
Deshalb steht der Mensch als Schwachstelle bei Cyber-Kriminellen immer öfter im Fokus des Angriffs, denn er kann die größte Sicherheitslücke einer Organisation darstellen. Ist er jedoch gewappnet, bietet er gleichzeitig ein großes Potential, um ein hohes Sicherheitsniveau zu erreichen. Daher ist es so wichtig, dass jeder Mitarbeiter für das Thema Phishing sensibilisiert wird, Angriffe dieser Art sicher erkennt und weiß, wie man sich professionell verhält.
Hierfür bietet die IT-Seal GmbH mit der Awareness Academy die Möglichkeit, im Unternehmen ein Phishing Awareness-Training durchzuführen. Dieses misst zum einen den Sicherheitsstandard gegenüber Social Engineering-Angriffen im Unternehmen, und ermöglicht es zum anderen, das Wissen und Sicherheitsbewusstsein der Mitarbeiter auf einen aktuellen Stand zu bringen. Allen Teilnehmern wird bei jedem “falschen” Klick auf unsere Phishing-E-Mails durch einen sogenannten teachable moment unmittelbar und mit geringem Aufwand aufgezeigt, Phishing-Angriffe zu erkennen und professionell zu handhaben.
Wir empfehlen sowohl Privatanwendern als auch Unternehmen gleichermaßen die folgenden Tools:
- Mit dem kostenfreien Lernkonzept NoPhish können die Grundregeln der Phishing-Erkennung spielerisch erlernt werden. Es ist sowohl als Online-Plattform als auch als iOS- und Android-App verfügbar. Mehr Informationen dazu finden Sie in unserem Blogeintrag zu NoPhish. NoPhish wurde entwickelt von SECUSO, einer Forschungsgruppe des KIT.
- Wenn Sie Thunderbird als E-Mail Client verwenden, können Sie das Add-On Torpedo herunterladen. Dieses Tool hilft Ihnen beim Erkennen schädlicher Links. Auch hierzu haben wir einen Blogeintrag veröffentlicht. Torpedo wurde entwickelt von SECUSO, einer Forschungsgruppe des KIT.
- PassSec+ für Mozilla Firefox erkennt unverschlüsselte Webseiten und warnt Sie bei der Eingabe von Login-Daten. Vor vielen Angriffen, bei denen Login-Daten abgegriffen werden sollen, sind Sie so geschützt. PassSec+ wurde entwickelt von SECUSO, einer Forschungsgruppe des KIT.
- Falls Ihr Bauchgefühl Sie warnt: Auf www.virustotal.com können Sie Links prüfen lassen, falls Sie sich nicht sicher sind, was das echte Ziel des Links angeht. Auch Dateien können hier geprüft werden – hier ist jedoch Umsicht geboten bei datenschutzrelevanten Dateien.
- Nutzen Sie verschiedene Passwörter für verschiedene Konten und ändern Sie diese regelmäßig – sonst haben potentielle Angreifer im schlimmsten Fall gleich überall Zugriff. Ein Passwortmanager (z.B. KeePass) kann helfen, den Überblick zu bewahren: Damit brauchen Sie sich lediglich ein einziges Masterpasswort zu merken.

Hinter IT-Seal (Social Engineering Analysis Labs) stecken IT-Sicherheitsexperten für den Aufbau einer nachhaltigen Sicherheitskultur. Wir helfen Unternehmen und ihren Mitarbeitern dabei, die Gefahren und Schäden durch Social Engineering-Angriffe auf ein Minimum zu reduzieren. Hierzu werden respektvolle aber effektive und authentische Angriffssimulationen durchgeführt. So wird zum einen der Sicherheitsstandard des Unternehmens messbar gemacht, zum anderen lernen alle Teilnehmer im sicheren Rahmen, mit Cyber-Angriffen umzugehen. Die Simulation von Angriffen erfolgt meist per E-Mail und beinhaltet unterschiedliche Schwierigkeitsgrade. Der Arbeits- und Datenschutz der teilnehmenden Mitarbeiter steht für uns stets im Vordergrund. In unseren Phishing-Auswertungen berichten wir nur über gruppenbezogenes Verhalten – das individuelle Verhalten wird zu keinem Zeitpunkt kommuniziert.
Wir verfolgen ein Full Service-Konzept und bieten mit unserer innovativen Awareness Engine bedarfsgerechtes Training: Teilnehmer, die Phishing-Angriffe schon sicher erkennen, werden nicht in ihrem Arbeitsalltag gestört. Klickt ein Mitarbeiter jedoch auf eine unserer Phishing-E-Mails, so wird ihm direkt am Beispiel dieser E-Mail aufgezeigt, wie er sie als solche hätte enttarnen können. Somit erhält jeder Teilnehmer genauso viel Training wie nötig, aber so wenig wie möglich.
Ziel ist es, Unternehmen dabei zu unterstützen eine aktiv gelebte Sicherheitskultur zu etablieren, die auf nachhaltig sensibilisierten Mitarbeitern basiert, die ihre Verantwortung für das Unternehmen kennen und wahrnehmen. Alle ziehen an einem Strang und erhöhen so die Sicherheit ihres Unternehmens.
Das klingt interessant? Testen Sie unsere kostenfreie Phishing-Simulation: Als Teilnehmer unserer Demo erhalten Sie innerhalb von zwei Werktagen vier Phishing-E-Mails. Falls Sie (aus Versehen oder aus Neugier) auf einen enthaltenen Link klicken, landen Sie auf unserer Erklärseite.
- Security Awareness messbar gemacht mit unserem ESI®: Der Employee Security Index ist ein wissenschaftlicher Benchmark zur Messung des IT-Sicherheitsbewusstseins (Security Awareness) in Organisationen. Er ermöglicht darüber hinaus eine Vergleichbarkeit. Welche Abteilung oder Branche ist wie sensibilisiert? Wo werden noch Maßnahmen benötigt? Mit dem ESI®, einer Kennzahl der Informationssicherheit, wird dies sichtbar.
- Wappnung gegen Spear-Phishing durch Kriminelle: Um die Mitarbeitenden bestmöglich für Angriffe von Cyber-Kriminellen zu sensibilisieren, haben wir die patentierte Spear-Phishing-Engine entwickelt. Diese sammelt öffentlich zugängliche Informationen aus Beruflichen Netzwerken (Open Source Intelligence, kurz OSINT) und erstellt darauf basierend realistische Spear-Phishing-Simulationen mit personalisierter Ansprache und authentischen Inhalten. Wir wollen, dass Mitarbeitende mit realitätsnahen und vertrauenserweckenden Nachrichten für den Ernstfall trainieren können. Wir betreiben kein generisches “Massen-Phishing”.
- Unser Mitgründer und CEO David Kelm ist ein versierter Social-Engineering-Experte: David Kelm beschäftigt sich seit 2012 dem Thema Social Engineering (Mitarbeitermanipulation durch Kriminelle). Für seine wissenschaftlichen Erkenntnisse rund um den “Faktor Mensch” in der IT-Sicherheit gewann Kelm den “Best-Student-Award” des Bundesamts für Sicherheit in der Informationstechnik (BSI). Er ist davon überzeugt, dass Mitarbeitende mit dem richtigen Lernansatz zur “menschlichen Firewall” ihres Unternehmens werden können – anstatt dessen Sicherheit zu gefährden.
- Unsere Arbeit basiert auf wissenschaftlichen Erkenntnissen: Unsere Maßnahmen für die Mitarbeitersensibilisierung gegen Spear Phishing sowie deren Erfolgsmessung basieren auf erfolgreicher Forschung. Mit David Kelm hat unser Start-up, das eine Ausgründung der TU-Darmstadt ist, darüber hinaus einen versierten Experten für Social Engineering, insbesondere Spear Phishing, an seiner Spitze.
- Datenschutz und Mitarbeiterfreundlichkeit Hand in Hand: Da wir Mitarbeitende sensibilisieren, aber nicht anschwärzen wollen, achten wir darauf, dass sie bei der Auswertung stets anonym bleiben. Wir evaluieren den Erfolg unserer Maßnahmen nur gruppenbasiert und unsere Datenverarbeitung erfolgt natürlich DSGVO-konform.
- Made in Germany: Die IT-Seal GmbH ist ein deutsches Unternehmen, das hauptsächlich auf den deutschen Markt spezialisiert ist. Hier ansässige Geschäftskunden bekommen somit von uns DSGVO-konforme Dienstleistungen, die auch in sonstiger Hinsicht die hier geltenden gesetzlichen Bestimmungen einhalten. Schon bei der Entwicklung unserer Lösungen stehen für uns Mitarbeiter- und Datenschutz im Vordergrund (“security & privacy by design”).
- Die deutschlandweit erste lokale Cyber-Security-Kampagne: Mit “Bleib wachsam, Darmstadt!” haben wir mit der Wissenschaftsstadt Darmstadt und der Digitalstadt Darmstadt eine bisher einmalige Initiative ins Leben gerufen, die Bürgerinnen und Bürgern ein kostenloses IT-Sicherheitstraining bietet und sie für Phishing sensibilisiert.
- Mehrfach ausgezeichnet: Für unsere Maßnahmen rund um Mitarbeitersensibilisierung und unsere Ideen für deren Mess- und Vergleichbarkeit haben wir folgende Preise gewonnen:
– 1. Platz als “Bestes Cybersecurity Startup Deutschlands” auf der it-sa
– 1. Platz beim europaweiten Social Engineering-Wettbewerb des TREsPASS_Projects
– “Top 10 der besten Cyber Security Startups Europas” beim SBA-Research-Wettbewerb
– “Best Student Award” des Bundesamts für Sicherheit in der Informationstechnik (Preisträger: Unser Mitgründer und Ideengeber David Kelm)
– 1. Platz beim europaweiten Social Engineering-Wettbewerb des TREsPASS_Projects
– “Top 10 der besten Cyber Security Startups Europas” beim SBA-Research-Wettbewerb
– “Best Student Award” des Bundesamts für Sicherheit in der Informationstechnik (Preisträger: Unser Mitgründer und Ideengeber David Kelm)
Mehr zu uns finden Sie auf “Warum IT-Seal?” Haben Sie Fragen? Wir freuen uns, von Ihnen zu hören!
IT-Sicherheitstraining für Privatpersonen:
Haben Sie Interesse an einem kostenfreien IT-Sicherheitstraining für sich, für Ihre Freunde und Familie? Dann melden Sie sich gerne bei Bleib wachsam, Darmstadt! an, eine Kampagne für alle Bundesbürger:innen.



