The election campaign in the US in 2016 was truly a special one: besides the unexpected outcome, various parties used new technologies combined with social engineering methods to influence voters for the first time.
Although Barack Obama already used social networks such as Facebook very successfully in 2008 and 2012, the newly elected President Donald Trump set new standards when he used social networks to specifically influence voters with microtargeting. How much impact this approach actually had on the election outcome is, of course, debatable and impossible to quantify precisely. Nor is it possible to quantify what influence the WikiLeaks publications by Hillary Clinton’s campaign manager and the Democratic National Committee (D.N.C.) had on the outcome of the election. However, it is obvious that the insight into these political backgrounds helped to strengthen the feeling of being deceived by the political elite.
These publications have an explosive history: As early as September 2015, the FBI had indications that at least one of the D.N.C.’s computers had been compromised by a team of hackers, which the U.S. side believed to be connected to the Russian government. However, the D.N.C. help desk employee suspected a “prank call” behind the FBI’s call and paid little attention to the incident. As a result, the attackers were able to stay on the D.N.C.’s network for seven months before any concrete action was taken to protect them.
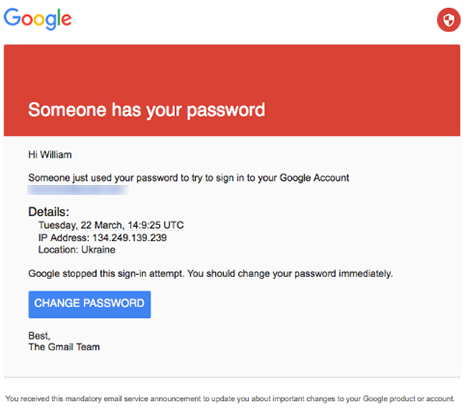
Meanwhile, another team of hackers started attacking journalists and politicians from different parties. To do so, they sent a spear phishing email with a warning from Google: “Someone just used your password to try to sign into your Google account”. The message spoke of a login attempt from Ukraine: “Google stopped this sign-in attempt. You should change your password immediately.” A Clinton campaign staffer clicked directly, giving access to his emails. An assistant to the chief campaign manager, however, suspected the fraud and so first checked with an IT staffer. He answered “This is a legitimate email. John needs to change his password immediately.” – a momentous mistake. Admittedly, the link was difficult to expose at first glance as a phishing attempt:
https://www.google.com/amp/tiny.cc/g8nmhy
http://myaccount.google.com-securitysettingpage.ml/security/signinoptions/password?e=[…]
Hidden behind this link is a redirection via the URL-Shortener service tiny. cc (tiny. cc/g8nmhy). In the present case, the victims were lured to a fake site. By means of a cloned Google login page, which could only be distinguished from the real one by the URL (com-securitysettingpage.ml), the login data was obtained.
In addition, the attackers also gained access to accounts of the D. N. C. and to the main D. N. C. network through a VPN. They were able to divert further information and data without hindrance – but the actual extent of the data flow is not conclusively known. Only the politically useful e-mails of the D. N. C. and the Clinton campaign, as well as some other data from the Clinton Foundation have been published so far.
And the Moral of the Story: Whoever has so much to lose, should better protect themselves thoroughly
At this time of year, we hear the moral of stories around the world: If Clinton campaign staff had been better informed, trained and protected about the threat of phishing attacks, chances are the hackers would have been fended off. The infections and leaks would not have occurred, the public would not have had the deep insight into political practices, and Clinton might have done better in the election. That’s why it’s important for employees to be able to detect cyber attacks. But that’s not how it happened – the world was enlightened, Trump won. All we can do is learn our own lessons: such as carry out preventive anti-phishing measures such as social hacking security trainings and risk analyses.





