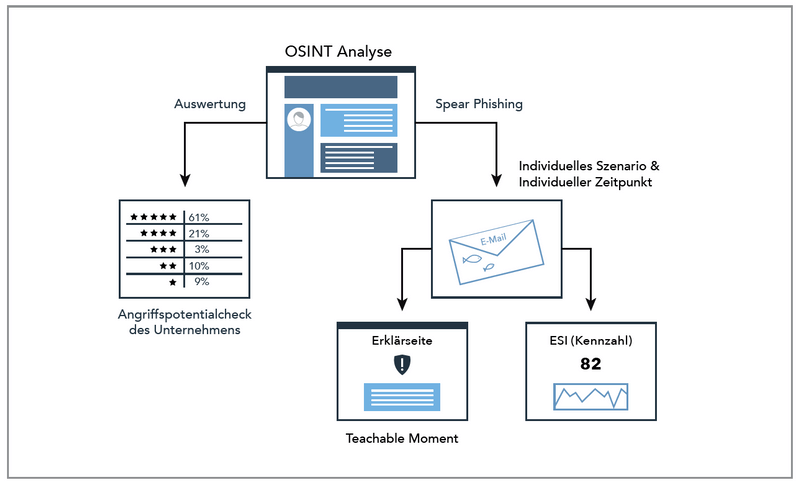
Today’s phishing emails are becoming more and more sophisticated. Spear Phishing is a term used to describe attacks that are carried out very purposefully against an organization or even an individual. The attackers usually begin to collect information from publicly available sources in order to obtain a profound image of the target person. According to the jargon of espionage, this step is called OSINT (Open Source Intelligence). The information collected is used to find the most credible pretext for contacting the target person. The aim is to provoke a visit to a website or the opening of a file in order to infect computers, steal sensitive information oder instruct wire transfers.
The OSINT analysis of your company: how much information is publicly available?
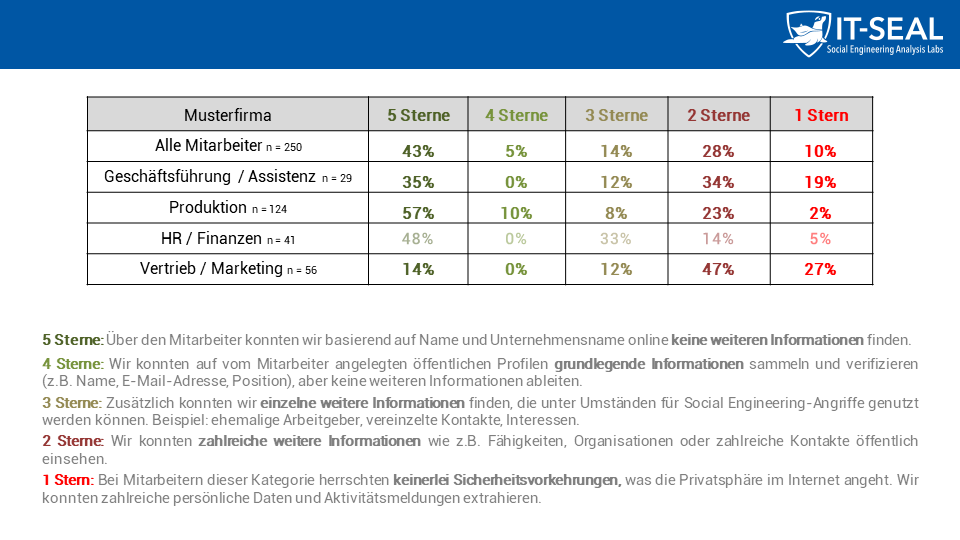
For you to assess how threatened your company is by information on social media, we have developed our “analysis of attack potential”. We analyze how much (critical) information employees disclose on professionally used social media and evaluate the results found anonymously.
Spear Phishing à la carte
In addition, we use the collected data to make our spear phishing simulations even more targeted: “Invitation to the company hiking group”, “I remember you worked for this company before – what do you think about this report” . “I would like to buy my first paragliding equipment. Can you give me a hint?”
This enables us to simulate not only mass phishing but also highly targeted spear phishing attacks. The simulation of this range of attack scenarios enables us to obtain a comprehensive picture of your risk situation and to calculate your individual ESI® zu berechnen.
Data protection is – always – a central component that must be taken into account. The fact that we only use publicly available information that has been published and released by the employee themself was considered legitimate by data protection officers. Privately used social media such as Facebook is not part of the IT seal analysis of attack potential. It is also important to us not to present any danger to employees: There is no personal evaluation – all data is stored pseudonymised, reported in aggregated form and protected by multi-level security concepts.





