The CEO fraud is a popular scam among online fraudsters, sometimes used to scam companies in the millions. The criminals forge e-mails or pretend to be the boss by phone and ask for urgent remittances. Business is booming, especially during the holiday season. CEO fraud is thriving. The attackers aim at SMEs in particular, but large corporations are also affected. The number of companies scammed by the CEO fraud pattern is constantly increasing. Especially in the summer months or around Christmas, when the workforce is thinned out, the risk increases: If an employee’s absence results in responsibilities being distributed differently, situations quickly arise in which the responsibility is not exactly clarified or the overview is missing. According to the FBI, the annual damage caused by CEO fraud amounts to 2.8 billion euros worldwide. In the German economic area, the Federal Criminal Police Office has counted 250 cases of fraud in the last three years. The best known in 2016 were the Bavarian automotive supplier Leoni AG (who lost 40 million euros) and the Austrian-Chinese aerospace supplier FACC (50 million euros). The number of unreported cases is expected to be high.
Social Engineering as a basis for the CEO-Fraud
The cyber criminals’ goal is to influence employees of a company in such a way that they transfer the company’s funds. To this end, the attackers spy on the personal and business environment of their victims, pretend identities and exploit human behaviours such as obedience to authority. The well-known trickster Frank Abagnale provides an illustrative example from the time before the internet existed. In the 1960s he was active as a con man and cheque cheater. His story was filmed under the title “Catch me if you can” in 2002. One scene shows Abagnale at the airport, watching all routines which involve money transfer. He intervenes in the process of transporting money from the ticket counter to a locking system by borrowing a uniform, standing next to the locker and attaching a note to it “Out of order – please hand it in to the security guard”. Social engineering was that simple as early as the 1960s; today, social platforms make it even easier to build relationships of trust even without direct physical contact. Attackers can sound out internal structures and the right contact persons without much effort. For the CEO fraud, the accounting and finance departments are of particular interest.
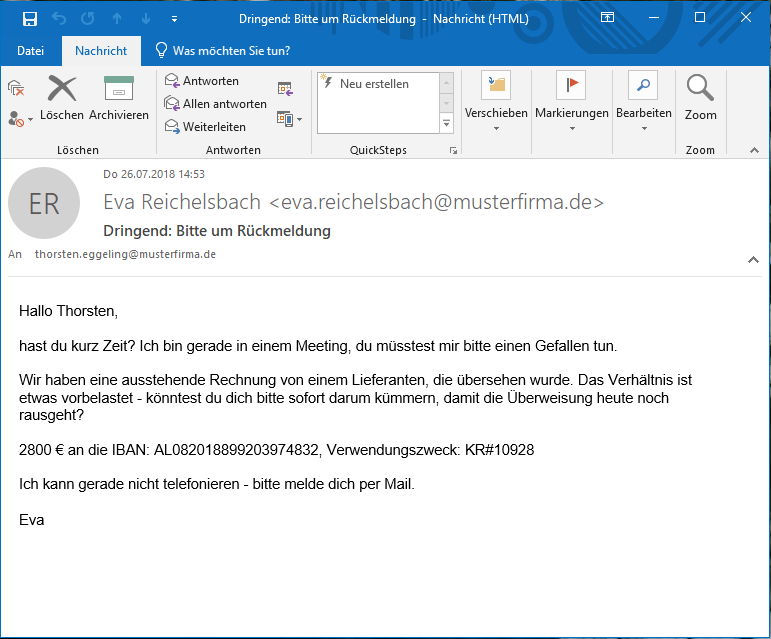
Spear phishing: payment order from the boss, prosecutor or auditor
Equipped with the right information, criminals use spear phishing to get to their destination. For example, the fraudsters forge an e-mail on behalf of a member of the management board and then impersonate the auditor who is allegedly responsible for the execution of the deal. Of course, the whole thing happens under the strict pretext of confidentiality, otherwise there are fictitious drastic consequences. Thus, large sums of money end up in foreign accounts, often without a chance of retrieving them.
Human firewall: Phishing awareness training is indispensable
Emails aimed at CEO fraud usually do not contain links or attachments that could be filtered out by the technical defense system. Often it is just a text that gives an order for payment under a pretext. This makes the user a “human firewall”, and continuous training in the area of phishing awareness is indispensable. If an employee is sensitized to the tricks of online fraudsters, e.g. through social engineering awareness training, it is more likely that an attempted CEO fraud will go the right way: the recipient asks the sender or superior and verifies the payment order on another channel before executing it.




